Overview
The latest release from 6clicks is their vulnerability management solution that bridges the traditional world of GRC and technical assurance. The 6clicks vulnerability management solution is for cybersecurity professionals, advisors and managed service providers (MSPs) looking for an integrated and more effective way to manage and communicate the holistic cybersecurity risk profile.
Along with integrating data from leading vulnerability scanning tools from vendors like Qualys and Nessus, 6clicks also provides the opportunity to define custom mappings to easily import vulnerabilities from any system. Vulnerabilities with their associated CVEs are then automatically linked to assets and easily correlated with risks and issues for remediation and ongoing prioritization.
“Our vulnerability management module presents a huge opportunity for cybersecurity professionals and makes it so much easier to manage cybersecurity risk overall – converging technical assurance with risk, governance and compliance,”
Dr Heather Buker, Global CTO of 6clicks, explained.
In a nutshell, the diagram below explains how the vulnerability management module works.
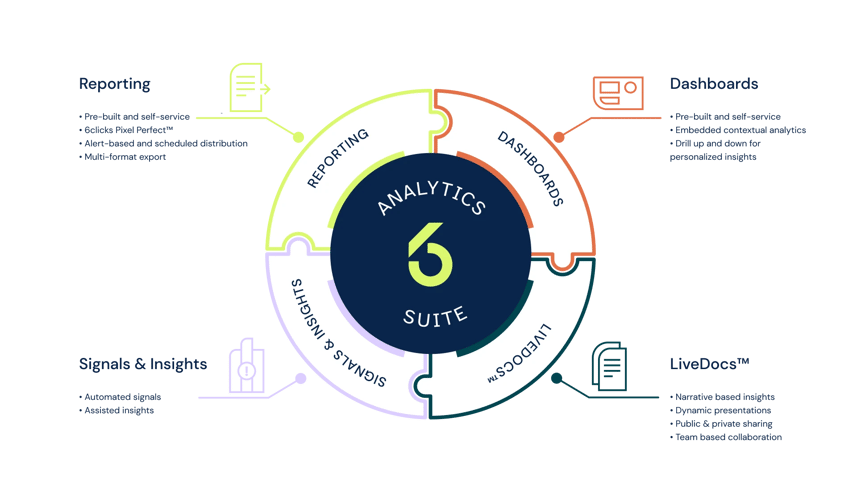
As Jim Tiller, Global CISO at Nash Squared explained,
“…risk is the bridge between GRC and vulnerability management.”
The 6clicks fully integrated GRC platform makes this possible by providing business context in risk management terms around the vulnerabilities.
The partnership opportunity for advisors and MSPs
For cybersecurity advisors and MSPs, the vulnerability management module is an opportunity to provide a further integrated service delivery offering, including managed services or vCISO. Along with streamlining service delivery, there’s a revenue-sharing opportunity as a 6clicks reseller or referral partner.
William Birchett, President of Logos Systems and part of the global vCISO network, explained that with 6clicks Vulnerability management, the opportunity for MSPs and those providing vCISO offerings is huge. He says,
“[vCISOs] can now understand what they’re communicating, how the organization’s risk is impacted by vulnerabilities, and how to prioritize [the vulnerabilities].”
Pricing
Pricing for the 6clicks vulnerability management module is made available via 6clicks partners or directly. More information is available here.
About 6clicks
Aside from being so fast to implement and easy to use, here’s 6clicks is making waves in the market:
- Its Hub & Spoke architecture is designed from the ground up to support federated or distributed deployment, which is perfect for large enterprises, advisors, and MSPs.
- Hailey, the 6clicks AI engine that takes seconds to perform compliance and policy gap analysis where it would otherwise take weeks, is a boon for compliance professionals.
- Fully integrated content all baked into the platform. No need for ‘uploads’, external data feeds, or issues due to lack of traceability.
As the name suggests, 6clicks makes it easy to manage risk and compliance in just 6 clicks. (Read more about this in the blog The founder’s story: How 6clicks was born and what’s behind the name). Designed for advisors and businesses, and powered by AI and integrated content, 6clicks is taking on giants like ServiceNow, OneTrust, RSA Archer, and Galvanize.
Watch the video here:
Written by Dr. Heather Buker
Heather has been a technical SME in the cybersecurity field her entire career from developing cybersecurity software to consulting, service delivery, architecting, and product management across most industry verticals. An engineer by trade, Heather specializes in translating business needs and facilitating solutions to complex cyber and GRC use cases with technology. Heather has a Bachelors in Computer Engineering, Masters in Engineering Management, and a Doctorate in Information Technology with a specialization in information assurance and cybersecurity.










