Between 2016 and 2018 I held the role of Chief Digital Officer at KPMG, responsible for strategy and the development of software assets to underpin key areas of the firm’s..
Most in-demand frameworks
Other topics

Keynote: Introducing 6clicks AI and the Enterprise Action...
In this keynote address, Ant, the CEO of 6clicks, introduces a groundbreaking approach to cybersecurity risk and compliance management through the development of two innovative..
Hailey Assist, The Future of AI and the 6clicks EAM
This conversation provides a fascinating glimpse into the innovative world of AI in cyber risk and compliance, as explored by 6clicks through their Hailey Assist AI tool. Media..
6clicks Partners with Microsoft to run 6clicks on Private...
Summary 6clicks, a cyber governance, risk, and compliance (GRC) platform, has partnered with Microsoft to offer a privately hosted option of its software. This collaboration..

Building an AI classification model for GRC software
Artificial intelligence (AI) and machine learning (ML) transform how businesses identify and respond to customer needs through user intent classification — an increasingly vital..
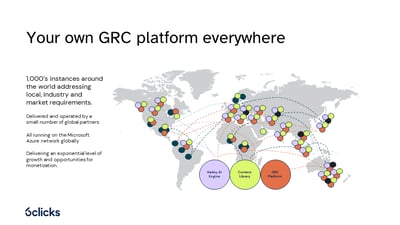
Empowering enterprises: Get in control with your own GRC...
In today's dynamic business landscape, enterprises are constantly seeking innovative solutions to streamline their operations, improve the value they deliver to their customers,..

6clicks Fabric for GSIs: Tailoring cybersecurity GRC...
Robust cybersecurity measures and the effective and safe implementation of IT infrastructure are critical for organizations to successfully do business in the modern digital..

Building an effective risk review process with 6clicks’...
Establishing an efficient risk review process is essential in executing a comprehensive risk management strategy. During the risk review process, an organization identifies..

6clicks GRC Platform Now Available on Microsoft Azure for...
New Capability Empowers Global Systems Integrators, Government, and Critical Infrastructure Sectors to Control Configuration, Distribution, Security, and Data Sovereignty

Global Systems Integrators: An approach to your GRC...
Discover the options when it comes to choosing GRC technology to support your advisory or managed services offerings.





