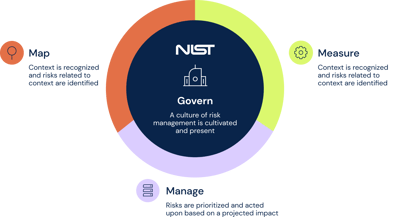
What is the NIST framework for cybersecurity?
The NIST Cybersecurity Framework (CSF) is a set of guidelines and recommendations developed by the National Institute of Standards and Technology (NIST) for improving cybersecurity and risk management at the organizational level. The CSF is not a mandatory standard, but rather a set of best practices that organizations can choose to adopt. The CSF was created in response to a request from the Obama administration in 2014.
What are the NIST framework profiles?
The NIST Cybersecurity Framework (CSF) allows organizations to create a customized plan for improving their cybersecurity posture and reducing risk. This plan, known as a "Profile," takes into account the organization's specific goals and priorities, as well as any relevant legal and regulatory requirements and industry best practices.
An organization may choose to have multiple profiles, each tailored to the needs of a particular component or area of the business. Profiles can be used to describe the current state of an organization's cybersecurity practices or to outline the desired target state.
The Current Profile in the NIST Cybersecurity Framework (CSF) describes the cybersecurity outcomes that an organization is currently achieving, while the Target Profile outlines the outcomes needed to reach the organization's desired cybersecurity risk management goals.
Profiles can help an organization effectively communicate its risk management practices and goals to all stakeholders, including partners, vendors, and other external organizations. By creating these profiles, an organization can more easily convey its current and target levels of cybersecurity risk and strength to others.
How to easily implement the NIST framework?
The NIST framework is a widely recognized and effective tool for managing cybersecurity risk, but it can be complex and may require customization to meet the specific needs and goals of an organization.
According to a survey conducted by Dimensional Research, 64% of respondents who were using the CSF reported that they were not implementing all of the recommended controls, and 83% of organizations planning to implement the CSF in the coming year intended to adopt only some of the controls.
While selective adoption of the CSF controls can be effective, it is important to find ways to simplify the framework and make it more manageable for an organization. Here are important steps to simplify and accelerate the implementation of the NIST framework for cybersecurity.
1. Align NIST framework with business goals
To effectively align an organization's cybersecurity program with its business objectives using NIST CSF, it can be helpful to map those objectives to the control families outlined in the framework. By focusing on the control families that are most relevant to the organization's specific goals, it can more effectively prioritize its efforts and allocate resources to address its most pressing concerns.
2. Start with the primary controls
To effectively implement the NIST Cybersecurity Framework (CSF) in an organization, it can be helpful to start by selecting a subset of the control families and focusing on the "Primary Controls" within those families. Primary Controls are the core set of controls that are essential for achieving the desired cybersecurity outcomes within a particular control family. By limiting the initial custom framework control list to the Primary Controls, an organization can focus on the most essential elements of the CSF and build a solid foundation for its cybersecurity program.
Once the Primary Controls are in place, the organization can then consider adding "Control Enhancements," which are additional details beyond the base control that can further enhance the effectiveness of the control. Control Enhancements might include factors such as the frequency of testing, automation of processes, and extensive documentation of control-related procedures. It is important to note that Control Enhancements should only be implemented once the base control is already in place, as they are meant to enhance rather than replace the core controls.
3. Implement NIST SP 800-171 first
One way for an organization to effectively select and implement the base controls for its cybersecurity program using NIST CSF is to start with an existing framework profile or selection, such as NIST SP 800-171. This standard covers more than 80% of the full NIST CSF but requires only about 20% of the effort to implement, making it a more efficient way to address a significant portion of the framework's controls.
4. Treat all 5 phases of NIST CSF equally
The NIST framework is structured around five phases that outline a logical process for managing cybersecurity risk: Identify, Protect, Detect, Respond, and Recover. To create a balanced and effective cybersecurity program using the CSF, it can be helpful to distribute effort equally across all five phases. This can help ensure that an organization is addressing all aspects of its cybersecurity posture and taking a holistic approach to risk management.
Final thoughts
The NIST framework is a comprehensive tool that can help organizations improve their cybersecurity posture and better protect against cyber threats. Many small and medium-sized businesses (SMBs) may have limited resources and face challenges in securing sufficient funding for cybersecurity measures. At the same time, a large cybersecurity budget does not necessarily guarantee protection against cyber attacks. It is often more important to have a strong security framework that can address specific risks effectively without compromising on security.
NIST CSF provides a structured approach to managing cybersecurity risk and can be an invaluable resource for any organization looking to strengthen its defenses against potential threats. While the implementation of the NIST framework might seem like a lot of work, automation can significantly cut down on time and effort. The 6clicks platform provides comprehensive support for implementing NIST CSF through integrated controls, ready-to-use content, and automation. Head to our solution page for more information - NIST CSF Compliance.
Want to know how you can achieve faster compliance with NIST CSF and other standards with the help of automation and AI? Get a demo of the 6clicks platform to see how we are helping businesses streamline information security and GRC.
Related useful resources
-
What do we know about NIST CSF 2.0?
-
NIST cybersecurity framework: Frequently asked questions answered!
-
6 cybersecurity frameworks for improving cyber health
Written by Andrew Robinson
Andrew started his career in the startup world and went on to perform in cyber and information security advisory roles for the Australian Federal Government and several Victorian Government entities. Andrew has a Masters in Policing, Intelligence and Counter-Terrorism (PICT) specialising in Cyber Security and holds IRAP, ISO 27001 LA, CISSP, CISM and SCF certifications.