The Essential 8 (E8) forms the Australian Signals Directorate's (ASD) and the Australian Cyber Security Centre's (ACSC) widely published guidance which aims to help build Australia’s cyber resilience and mitigate against common cyber threats.
Along with the core requirements, and assessment templates, 6clicks has now released an embedded report template based on ASD guidance. This can further help businesses, advisors and MSPs streamline assessment and reporting processes related to the E8.
What is the Essential 8 maturity model?
The E8 is an Australian cybersecurity maturity model first published by ASD in 2017 and last updated in November 2022. The aim of the model is to protect businesses from increasingly frequent and sometime sophisticated cyber attacks. Originally designed to protect Microsoft Windows-based networks, the E8 can also be applied to cloud services or other operating systems.
However, when applying the controls to other environments, organisations will most likely need to translate the principles behind the E8 and include some additional considerations that apply to these environments. The guidelines provided by the Australian Cyber Security Centre (ACSC) based on their cyber threat reports provide the additional support to effectively apply the Essential 8 in different environments.
The Essential 8 maturity model was created to effectively implement the ASD E8 controls. It is based on the longer Top 37 strategies to mitigate cyber incidents and adds to the proceeding Top 4 security controls which was too lean to provide sufficient protection. As a first step to implementing the ASD E8, the maturity level of an organisation’s existing cybersecurity strategies needs to be determined.
There are 4 maturity levels for organisations that can use as a guideline for implementing the Essential 8 model.
Maturity level zero
This level isn't actually a maturity level and serves to indicate that the organisation’s strategy is not aligned with the threat environment and the cybersecurity posture is weak. When the weaknesses are exploited the organisation is likely to experience a notable impact on confidentiality, integrity, and/or availability of their systems and data.
Maturity level one
This maturity level indicates that the organisation is only partly aligned with the intent of the threat mitigation strategy. It may have some basic cyber hygiene controls in place to protect against opportunistic adversaries finding obvious points of vulnerability.
Maturity level two
This maturity level indicates that the organisation that the organisation’s cybersecurity strategy is mostly aligned with threat mitigation strategies. The organisation has protection against adversaries that exploit weaknesses in the cybersecurity approach through additional resources compared to maturity level one.
Maturity level three
This maturity level indicates that an organisation is fully aligned with the strategy for threat mitigation. The organisation has protection against adversaries with sophisticated tools and techniques. These organisations have a good level of capabilities for monitoring, detecting, and responding to cybersecurity threats.
Learn more in our blog here: The essential 8 maturity model for cyber security.
How does the ASD Essential 8 structured reporting template work?
In order to implement the ASD Essential 8 model, the current level of security needs to be assessed.
The ASD Essential 8 assessment report template is now available for download from the 6clicks Content Library. This template is based on the ACSC guidelines and can be used to standardise assessment reports and their interpretation.
The ASD Essential 8 structured report is an automatically generated report based on the ASD Essential 8 assessment template. It uses the 6clicks Pixel Perfect reporting engine to create stunning reports that can be exported as a document for review.
So, the process is as simple as this:
Step 1. Import the ASD Essential 8 content bundle from the 6clicks Content Library.
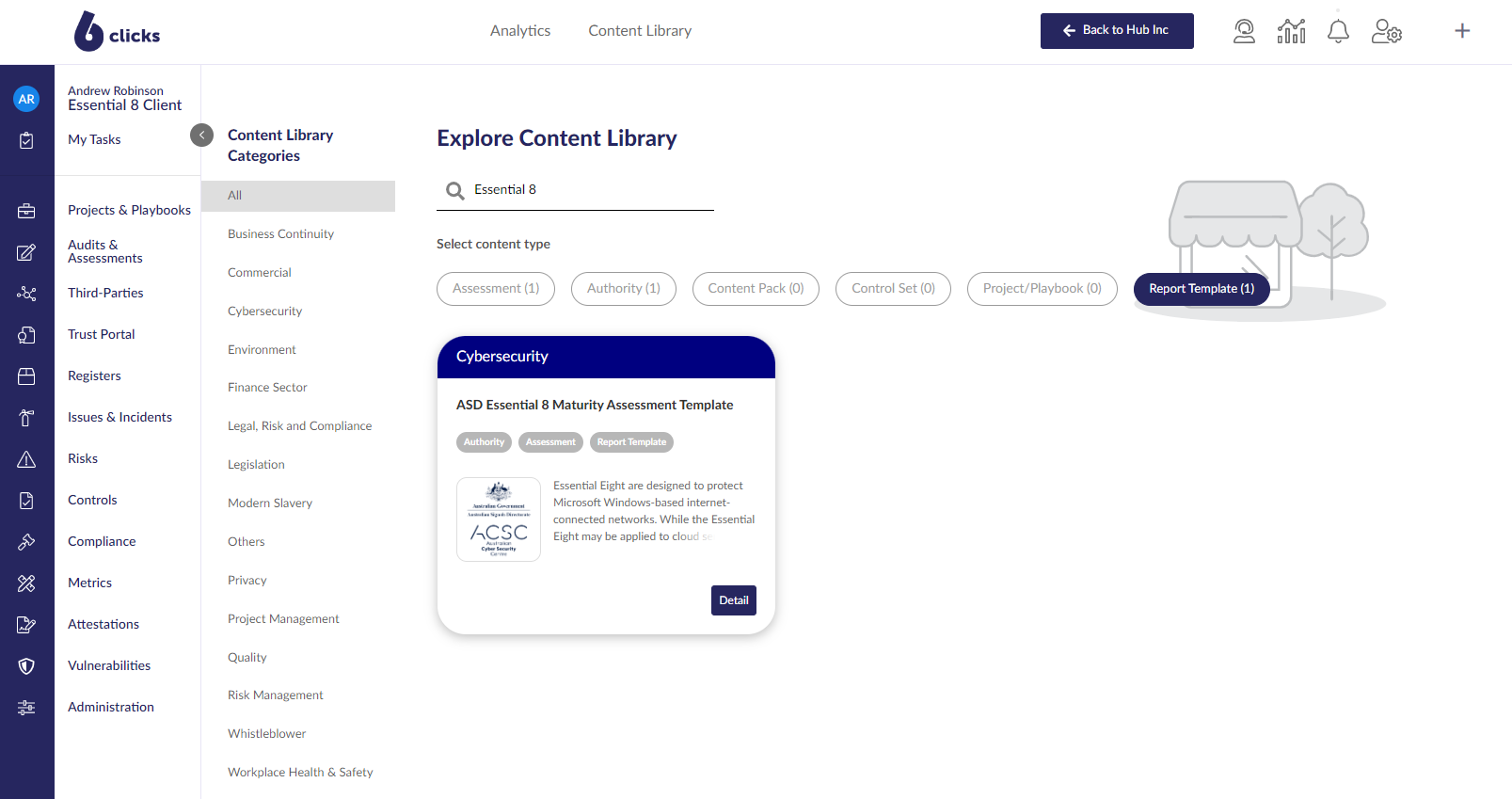
Step 2. Run the ASD Essential 8 assessment, and collect related evidence.
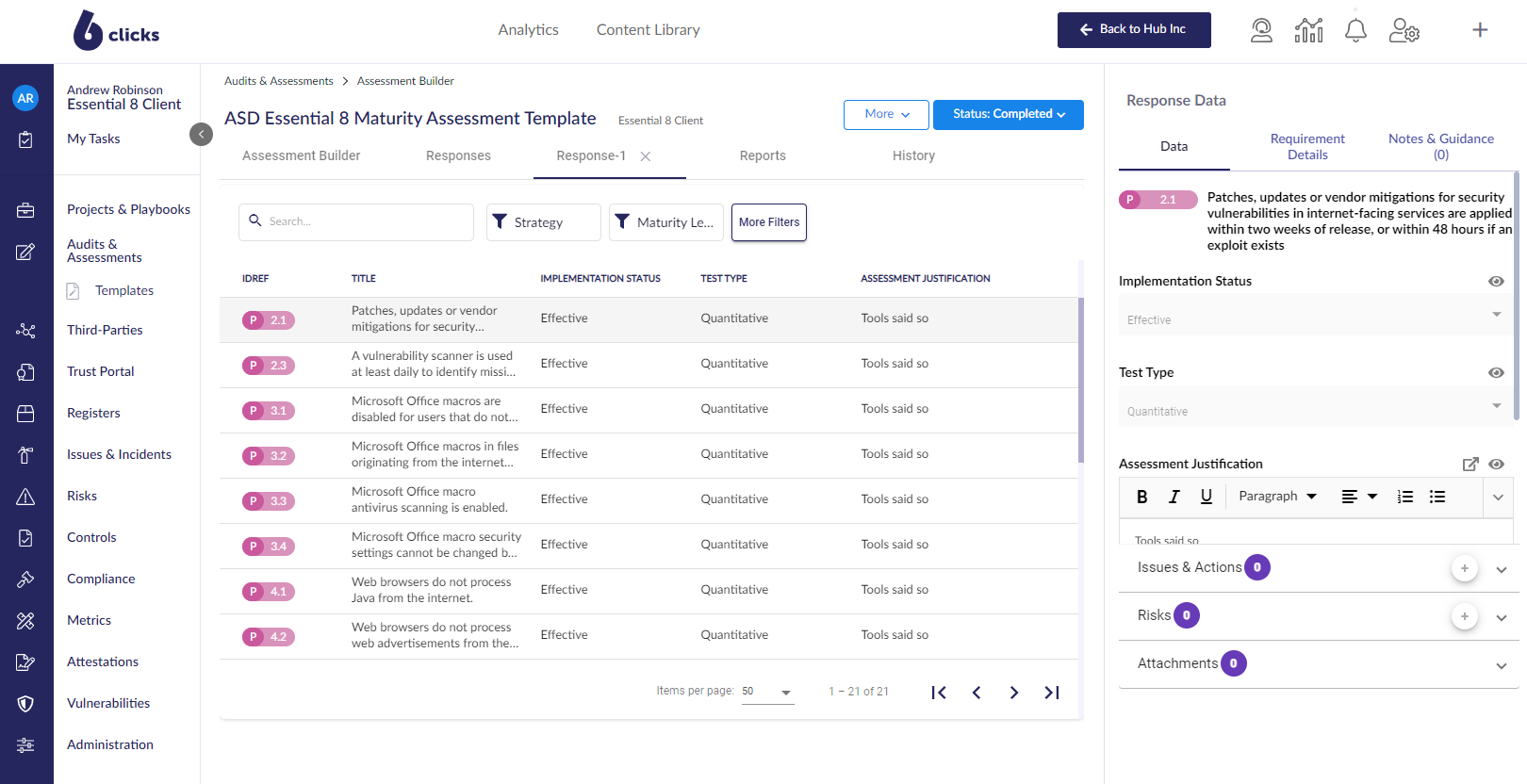
Step 3. Identify related risk, actions and findings associated with your assessment.
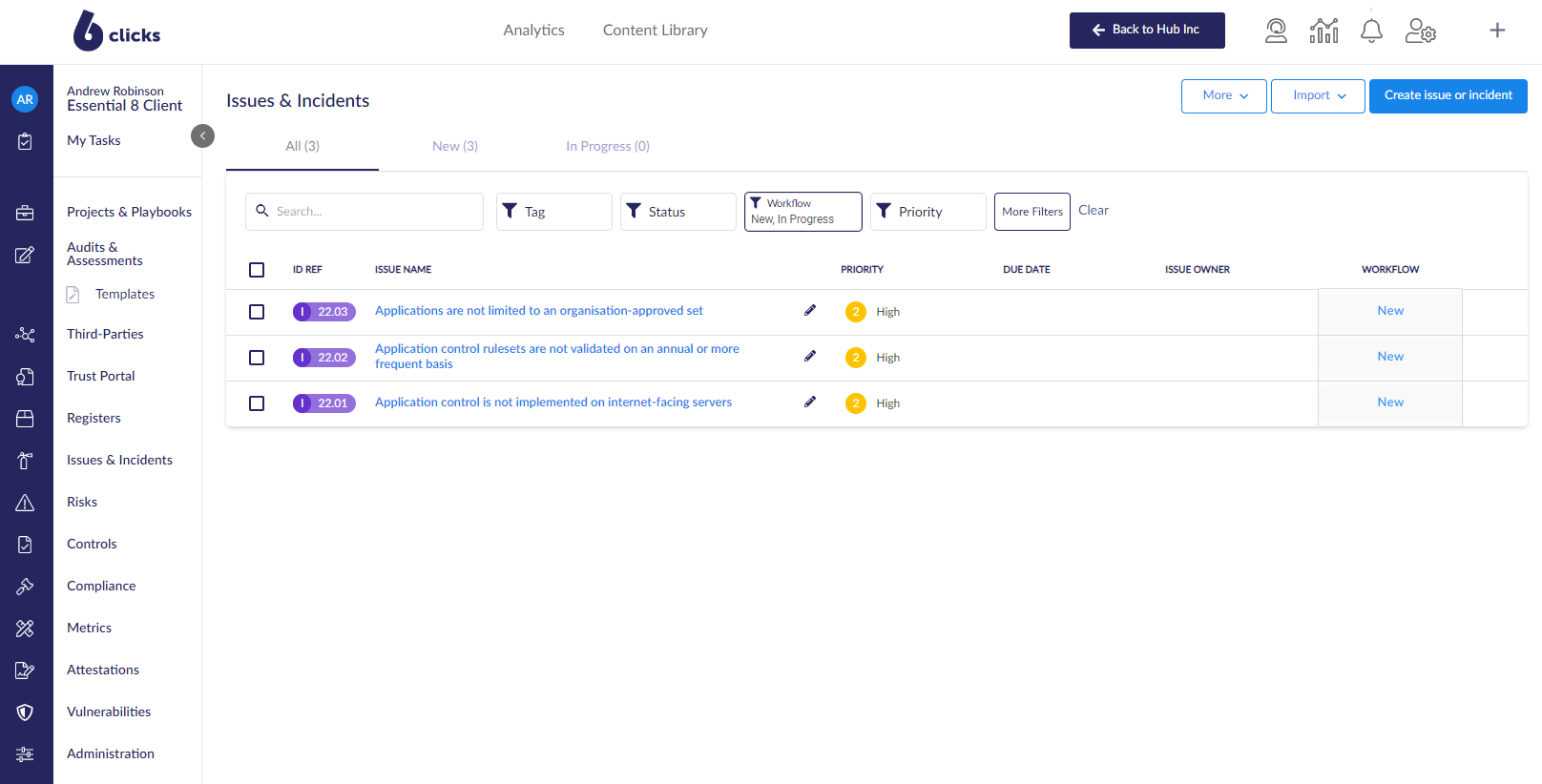
Step 4. Automatically generate your ASD Essential 8 report.
How this new reporting template can help advisors and MSPs with client's ASD Essential 8 compliance?
The template can be downloaded and used by advisors or MSPs for helping their clients carry out assessments or it can be used as a baseline to create your own assessments for branding purposes. You can add your brand to the template. However, all sections within the template must be used in the assessments created.
While using the template can help advisors and MSPs improve the quality of assessments for their clients, the 6clicks Reporting & Analytics suite also significantly improves the service delivery making it more streamlined and faster.
To know more about how 6clicks can help advisors and MSPs in implementing ASD Essential 8 and many other standards and frameworks, book a demo with us.
Discover how the 6clicks solution for ASD Essential 8 can help automate your risk management and compliance.
Written by Andrew Robinson
Andrew started his career in the startup world and went on to perform in cyber and information security advisory roles for the Australian Federal Government and several Victorian Government entities. Andrew has a Masters in Policing, Intelligence and Counter-Terrorism (PICT) specialising in Cyber Security and holds IRAP, ISO 27001 LA, CISSP, CISM and SCF certifications.