The digital age is revolutionizing business operations at every level, presenting both opportunities and challenges. Australian businesses can leverage technologies like the cloud, machine learning, and mobile devices to enhance efficiency and reduce costs. However, these very technologies also expose businesses to increasingly sophisticated cyberattacks.
To effectively manage cybersecurity incidents, it's crucial to adopt best-practice strategies as a starting point. The Australian Signals Directorate (ASD) and Australian Cybersecurity Centre (ACSC) have developed the Essential 8 Model, a government-led cybersecurity initiative. By following these strategies as general guidelines, businesses can quickly improve their cybersecurity posture without extensive investments or research.
To help you understand the benefits of the ASD Essential 8 maturity model for your enterprise or startup, we've organized this article into four sections:
- Introducing the ASD Essential Eight
- Preparing to Use the Essential Eight
- Implementing the Essential Eight
- Easily Assessing against the Essential Eight
Introducing the Essential 8 Maturity Model
The Essential Eight provides practical guidelines to mitigate cybersecurity incidents, including preventing malware delivery and execution, limiting the extent of cybersecurity incidents, and ensuring data recovery and system availability. According to cyber.gov.au, implementing the Essential Eight makes it significantly harder for adversaries to compromise systems. Proactive implementation of the Essential Eight can be more cost-effective in terms of time, money, and effort compared to responding to a large-scale cyber security incident. While businesses operating in high-risk environments may require additional guidance, assessing against the Essential Eight serves as a basic and affordable guide to prevent cyberattacks and related risks.
Preparing to Use the Essential 8 Maturity Model
Before implementing the mitigation strategies outlined in the next section, it is crucial to consider the following:
-
Identify which systems require protection: Determine which systems store, process, or communicate sensitive or easily accessible information.
-
Identify likely adversaries: Identify the adversaries most likely to target your systems, such as nation-states, cybercriminals, or malicious insiders.
-
Determine required protection level: Select mitigation strategies based on the risks posed by specific adversaries to business activities.
Implementing the Essential 8 Maturity Model
The Essential Eight encompasses strategies categorized into three key areas. Here's an overview of each strategy:
Strategies to Prevent Malware Delivery and Execution:
-
Whitelist applications: Control the programs allowed to run on your company's network to reduce exposure to malware attacks. Gradually implement whitelisting starting with high-level and high-risk users.
-
Patch software: Keep applications up to date by patching or mitigating computers with software flaws that can enable ransomware spread within 48 hours.
-
Block untrusted Microsoft Office macros: Configure Microsoft Office macro settings to block macros from the internet, allowing only vetted macros from trusted sources.
-
Fortify user applications: Configure web browsers to block Flash, ads, and Java on the internet. Disable unnecessary features in Microsoft Office, web browsers, and PDF viewers.
Strategies to Limit the Extent of Cybersecurity Incidents:
-
Restrict access privileges: Limit administrative privileges based on user duties, and provide extra confirmation steps for those with administrative access. Regularly review and manage access privileges using a centralized system.
-
Enable multi-factor authentication: Implement stronger user authentication using at least two methods, such as passwords, security keys, physical tokens, biometrics, and smartcards.
-
Update operating systems: Apply patches for security vulnerabilities in operating systems like Windows 10 and macOS as soon as they're released. Avoid using unsupported versions.
Strategies to Ensure Data Recovery and System Availability:
- Back up your systems daily: Regularly back up systems to ensure information can be recovered following a cybersecurity incident. Store multiple copies locally, on USB drives, and in the cloud. Test restoration periodically and after any IT infrastructure changes.
Easily Assessing against the Essential Eight
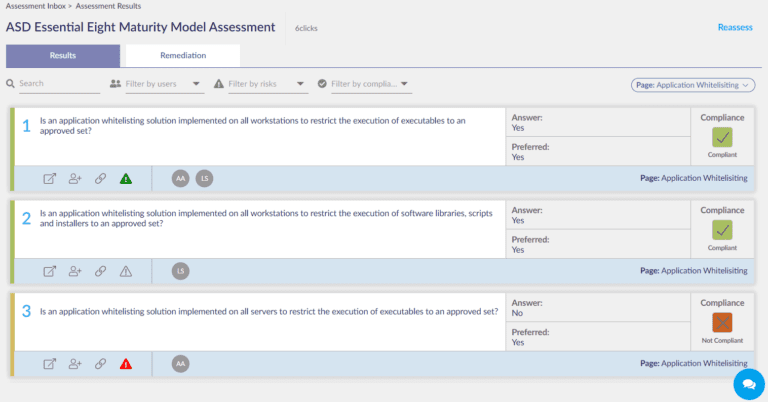
For an easier, digital implementation of the ASD Essential 8 for cybersecurity, consider using the 6clicks platform. Preventative maintenance plays a fundamental role in effective cybersecurity management, and the Essential Eight provides a comprehensive starting point for Australian businesses. Implementing these strategies correctly can help businesses avoid the devastating costs associated with major cyber breaches. Sign up or visit www.6clicks.com to learn more about assessing and improving your cybersecurity posture using 6clicks' tools.
Written by Louis Strauss
Louis is the Co-founder and Chief Product Marketing Officer (CPMO) at 6clicks, where he spearheads collaboration among product, marketing, engineering, and sales teams. With a deep-seated passion for innovation, Louis drives the development of elegant AI-powered solutions tailored to address the intricate challenges CISOs, InfoSec teams, and GRC professionals face. Beyond cyber GRC, Louis enjoys reading and spending time with his friends and family.