The definition of an ISMS framework
An Information Security Management System (ISMS) framework is a systematic approach to managing security risks, policies, and controls within an organization. It provides a holistic approach to protect the confidentiality, integrity, and availability of sensitive company information, as well as the underlying assets that support its operations. By implementing an ISMS framework, organizations can address both internal and external security threats, ensuring that a robust defense is in place to safeguard against unauthorized access, data breaches, and other security incidents.
At the core of an ISMS framework is the establishment of security policies, based on international standards such as ISO/IEC 27001. These policies outline the organization's commitment to security management, defining the security requirements and expectations for employees, suppliers, and other stakeholders. The framework also encompasses risk assessments, which identify potential risks to the organization's assets, allowing for informed decisions on which security controls and measures should be implemented.
In addition, an ISMS framework includes regular internal audits and reviews, ensuring that security practices are being followed and compliant with the established policies. It also encompasses ongoing maintenance to security policies, as the threat landscape evolves and new security risks emerge. To support the effectiveness of the ISMS framework, organizations often provide regular security awareness training to employees, promoting a culture of security and minimizing the risk of human error.
Explore the 6clicks solution to implement your ISMS.
Purpose of the ISMS framework
The purpose of the ISMS framework is to align IT and business security, effectively manage information security in all activities and provide guidance on proper ISMS implementation.
An ISMS framework, such as ISO 27001, serves as a comprehensive system for organizations to establish, implement, monitor, maintain, and improve their information security management. By adopting this framework, organizations can ensure that their IT and business security efforts are aligned, allowing for a more efficient and integrated approach to safeguarding sensitive information.
The ISMS framework helps organizations manage information security by providing a structured and systematic approach to identifying, assessing, and managing security risks. It establishes a framework of policies, procedures, and controls that help protect organizational assets from security threats and breaches. Additionally, the framework supports the development of best-practice guidelines for implementing effective security measures, including access control policies, security risk assessments, and regular internal security audits.
ISO 27001 is the most common and internationally recognized ISMS framework. It is based on a holistic approach to information security management and provides organizations with a framework that can be tailored to their specific needs and requirements. By implementing ISO 27001, organizations can demonstrate commitment to information security, improve their security posture, and effectively manage the risks associated with the use of information and technology. Overall, the purpose of the ISMS framework is to enable organizations to protect their sensitive information, maintain business continuity, and safeguard their reputation.
Components of ISMS framework
An ISMS framework consists of several key components that work together to ensure the effective management and protection of an organization's information security. These components include security policies, security controls, risk assessments, asset management, human resource security, and business continuity management. Security policies serve as the foundation of the framework, providing guidelines and rules for security practices. Security controls are the measures and safeguards put in place to mitigate security risks and protect against unauthorized access. Risk assessments help identify and prioritize potential risks to the organization, allowing for informed decisions on implementing security measures. Asset management ensures the proper identification, classification, and protection of organizational assets, such as intellectual property. Human resource security focuses on employee awareness, training, and managing the human element of security. Lastly, business continuity management ensures that the organization can recover and continue operations in the event of security incidents or disruptions. By implementing these components, organizations can establish a robust and comprehensive security management system in accordance with international standards.
Security policies
The security policies within the ISMS framework play a crucial role in enhancing information security and ensuring alignment with national and local regulations. These policies serve as guidelines and procedures that safeguard valuable data and ensure compliance with security requirements.
By implementing security policies, organizations establish a systematic approach to manage security risks and protect sensitive information. These policies provide a framework of best-practice guidelines for establishing security controls and measures that mitigate potential risks.
In addition, security policies facilitate the development of a holistic approach within an organization towards information security. They help in setting clear expectations and standards for employees, enabling them to make informed decisions and take appropriate actions to protect organizational assets.
Furthermore, security policies incorporate the necessary measures to defend against security threats and unauthorized access. Regular security awareness training and internal audits are conducted to assess the effectiveness of these policies, identify vulnerabilities, and make necessary improvements.
By adhering to security policies mandated by the ISMS framework, organizations are better equipped to address security breaches and incidents, resulting in enhanced protection of intellectual property, business continuity, and a stronger defense against evolving security risks.
Risk assessments and management
In the ISMS framework, risk assessments and management play a crucial role in ensuring the overall security and protection of organizational assets. This process involves the systematic identification, analysis, evaluation, and treatment of risks associated with information security.
The first step in risk assessments is the identification of potential risks. This includes considering both internal and external factors that could pose a threat to the organization's security, such as human error, security breaches, or environmental hazards. By thoroughly examining the threat landscape, organizations can better understand the potential risks they face.
Once risks are identified, a comprehensive analysis is conducted to assess their potential consequences, likelihood, and potential rewards. This step helps organizations gain a deeper understanding of the impact each risk may have on their operations and the potential benefits of addressing these risks effectively.
Based on the analysis, risks are then evaluated to prioritize their significance and determine the appropriate treatment options. These treatment options include risk modification (changing the likelihood or consequences of a risk), risk avoidance (eliminating the risk altogether), risk sharing (transferring the risk to a third party), risk retention (accepting and managing the risk internally), risk enhancement (capitalizing on opportunities that arise from the risk), and risk exploitation (actively seeking out and maximizing the potential benefits of the risk).
To effectively manage risks, organizations create and implement mitigation policies based on the identified treatment options. These policies outline the specific actions and measures necessary to reduce, eliminate, or accept risks, ensuring that appropriate security controls and measures are in place to protect sensitive information and mitigate potential vulnerabilities.
Adhering to the ISO 27001 standard, the ISMS framework emphasizes the importance of a systematic and proactive approach to risk assessments and management. By considering the consequences, likelihood, and potential rewards of risks and opportunities, organizations can make informed decisions and prioritize their efforts to ensure the best possible security outcomes.
Asset management
Asset management is a critical component of the ISMS framework as it helps organizations identify, value, and protect their important assets. This includes not only physical assets such as equipment and infrastructure but also information assets such as intellectual property and sensitive data.
The process of asset management begins with a thorough review and documentation of the organization's business processes and procedures. This step is crucial as it allows organizations to identify the assets that are critical to their operations and determine the appropriate security controls to implement.
By reviewing and documenting business processes and procedures, organizations can identify any potential vulnerabilities or gaps in their current security measures. This information is then used to develop a comprehensive asset management plan that outlines the specific security controls and measures required to protect the identified assets.
Successful asset management also requires the allocation of appropriate resources. Organizations need to allocate sufficient people, technology equipment, and finances to effectively implement security controls. This includes having qualified personnel who can oversee the asset management process, utilizing the latest technology and tools to monitor and protect assets, and allocating the necessary financial resources to support the implementation and maintenance of security controls.
Access control policies & procedures
Access control policies and procedures are essential components of the ISMS framework, providing a systematic approach to limit access to authorized personnel and protect sensitive business information. These policies outline the rules and guidelines for granting and managing access privileges within an organization's network and systems.
One crucial aspect of access control policies is the implementation of user authentication measures, such as passwords, biometrics, or two-factor authentication. These measures ensure that only authorized personnel can access the organization's resources and systems. Regularly updating and enforcing strong password policies play a significant role in preventing unauthorized access.
Additionally, access control procedures involve the continuous monitoring of network traffic for any anomalous behavior or unauthorized access attempts. Intrusion detection systems (IDS) and firewall configurations are commonly used to identify and respond to potential security breaches swiftly. These measures provide an additional layer of protection by detecting and mitigating potential risks.
Well-defined roles and responsibilities are fundamental in assigning access permissions. Access should only be granted to individuals who require it to perform their job functions. Regular reviews and audits of access privileges help to ensure that access remains appropriate and aligned with an individual's role.
Security measures & controls
Within the ISMS framework, various security measures and controls should be implemented to protect organizational assets and mitigate security risks. These measures ensure that the organization follows a systematic approach in maintaining the security of its information and resources.
One of the key security measures is the implementation of access controls. These controls include user authentication measures such as passwords, biometrics, and two-factor authentication. By enforcing strong password policies and regularly updating them, unauthorized access can be prevented.
Another crucial security measure is the use of intrusion detection systems (IDS) and firewall configurations. These measures continuously monitor network traffic for any abnormal activity or unauthorized access attempts. By promptly identifying and responding to potential security breaches, these measures help mitigate risks and protect organizational assets.
Furthermore, well-defined roles and responsibilities play a significant role in assigning access privileges. Regular reviews and audits of access privileges ensure that access remains appropriate and aligned with an individual's role. This helps to prevent any unauthorized access and strengthens asset protection.
In addition to access controls, other recommended security controls include regular security awareness training, internal security audits, and implementing best-practice guidelines and standards such as ISO/IEC 27001. These controls enhance the organization's ability to identify and respond to security threats, reduce human error, and make informed decisions.
Human resource security
Human Resource Security is a vital component of information security within organizations. The International Organization for Standardization (ISO) has recently introduced new and refined controls in this area through ISO 27001:2022. These controls aim to protect the organization's interests and ensure that personnel have the necessary security clearances.
One of the primary controls in Human Resource Security is personnel screening. This involves conducting background checks and verifying the qualifications and credentials of individuals before hiring them. By thoroughly assessing potential employees, organizations can mitigate the risk of hiring individuals with malicious intent or inadequate security awareness.
Another important aspect of Human Resource Security is information security awareness. Organizations need to provide regular training and awareness programs to educate employees about security policies and procedures. This helps ensure that personnel are aware of their roles and responsibilities in maintaining a secure working environment.
ISO 27001:2022 emphasizes the need for organizations to have a clear framework for managing Human Resource Security. This includes defining job descriptions, roles, and responsibilities, as well as implementing controls for authorization and access management.
Regulatory bodies & standards
When it comes to implementing an effective Information Security Management System (ISMS), organizations must adhere to various regulatory bodies and standards. One such critical ISO standard is ISO 27001:2022, which provides guidelines and best-practice recommendations for establishing, implementing, maintaining, and continually improving an ISMS.
ISO (International Organization for Standardization) and IEC (International Electrotechnical Commission) are two major regulatory bodies responsible for developing and maintaining international standards. Together, they form a joint committee known as ISO/IEC JTC 1/SC 27, which focuses on IT security techniques, including the ISMS framework.
ISO 27001 is designed to help organizations comply with a wide range of regulatory requirements and security standards. By adopting ISO 27001, companies can demonstrate their commitment to implementing a systematic approach to managing security risks and protecting sensitive information.
Compliance with ISO 27001 also allows organizations to align with other related standards, such as ISO 9001 for quality management systems and ISO 20000 for IT service management. This alignment promotes a holistic approach to security management and ensures that security practices are integrated into various organizational processes.
In summary, regulatory bodies like ISO and IEC play a crucial role in establishing global standards for information security. By adhering to ISO 27001 and related standards, organizations can benefit from a comprehensive framework that addresses security risks, regulatory requirements, and best-practice guidelines, ultimately enabling them to safeguard their assets and make informed decisions regarding security management.
Internal audits & reviews
Internal audits and reviews are crucial components of the ISMS (Information Security Management System) framework, serving as an ongoing process to evaluate the effectiveness of security controls and ensure ongoing compliance with legal and regulatory requirements.
Regular internal audits play a vital role in assessing the effectiveness of security controls implemented within an organization. By conducting thorough audits, businesses can identify potential gaps and vulnerabilities in their security measures and take necessary actions to address them. This proactive approach helps mitigate security risks and ensures the protection of sensitive information.
Moreover, internal audits help organizations maintain legal and regulatory compliance. By systematically reviewing security policies, practices, and procedures, businesses can identify any deviations from the required standards and take corrective actions promptly. This ensures that the organization remains compliant with relevant laws and regulations, minimizing the risk of legal and financial penalties.
To conduct internal audits effectively, proper documentation of procedures and business processes is essential. This documentation includes policies, guidelines, and operating procedures that act as a reference point for audit activities. By documenting these processes, organizations can demonstrate their commitment to security management and provide auditors with clear guidance on how to assess security controls.
In conclusion, internal audits and reviews are critical for ensuring the ongoing effectiveness of security controls and compliance with legal and regulatory requirements. By conducting regular internal audits and maintaining proper documentation, organizations can continuously improve their security posture and mitigate potential risks.
Business continuity management
Business continuity management is a critical component of the ISMS framework, as it helps organizations with risk management and disruptions that can impact their business operations. By implementing effective business continuity measures, organizations can ensure the continued availability of their products and services, minimize the impact of disruptions, and safeguard their reputation.
To assess and manage the risks associated with potential disruptions, organizations need to conduct a comprehensive risk assessment. This involves identifying potential risks and evaluating their likelihood and impact on business operations. By understanding the potential risks, organizations can prioritize their resources and implement appropriate measures to mitigate or respond to these risks.
Key components of business continuity management include the development and maintenance of a business continuity plan. This plan outlines the actions and strategies that need to be taken during and after a disruption to ensure the ongoing operations of the business. It includes elements such as backup and recovery procedures, alternative communication channels, and temporary relocation plans.
Other activities involved in business continuity management include regular testing and updating of the plan, raising awareness among employees through training and education, and establishing clear roles and responsibilities for responding to disruptions. It is also essential to regularly review and assess the effectiveness of the business continuity measures to identify any gaps or areas for improvement.
In conclusion, business continuity management is crucial within the ISMS framework as it enables organizations to assess and manage risks associated with potential disruptions. By implementing a robust business continuity plan and conducting regular assessments, organizations can ensure the continuity of their business operations and minimize the impact of disruptions.
Intellectual property protection
Intellectual property (IP) protection plays a crucial role in the ISMS (Information Security Management System) framework, helping organizations comply with industry regulations and safeguard their valuable assets. As organizations increasingly rely on digital information and technology, protecting intellectual property has become a top priority.
While IT security focuses on securing technology infrastructure, information security encompasses the broader goal of protecting all forms of information, including intellectual property. Intellectual property refers to creations of the mind, such as inventions, designs, and artistic works, that are legally protectable and valuable to organizations.
Within the ISMS framework, key components of intellectual property protection include identifying and classifying intellectual property assets, implementing appropriate access controls to prevent unauthorized access, and monitoring and detecting potential threats or breaches. Organizations should also establish policies and procedures for handling intellectual property, including clear guidelines for employees on how to protect and handle sensitive information.
Best-practice guidelines for safeguarding intellectual property within the ISMS framework include regular training and awareness programs to educate employees about the importance of IP protection. Additionally, organizations should implement measures such as encryption, data loss prevention tools, and secure data storage to enhance intellectual property security. Regular audits and assessments are also essential to ensure compliance with industry regulations and identify potential vulnerabilities that may put intellectual property at risk.
A systematic approach to security requirements
The systematic approach to security requirements within the ISMS framework ensures that organizations can effectively protect their information and assets. This approach involves a structured and comprehensive analysis of security risks, the development of policies and processes, and the continuous improvement of security measures.
To begin, organizations need to identify and assess potential security risks. This involves conducting a thorough risk assessment to understand the vulnerabilities and threats that may impact the organization's information and assets. By identifying these risks, organizations can prioritize their efforts and allocate resources to address the most critical security concerns.
Once the risks have been identified, organizations can develop policies and processes to mitigate these risks. This includes defining clear and specific security objectives, setting up appropriate security controls, and establishing procedures for monitoring and responding to security incidents. By implementing these policies and processes, organizations can ensure that their security measures are aligned with their business objectives and regulatory requirements.
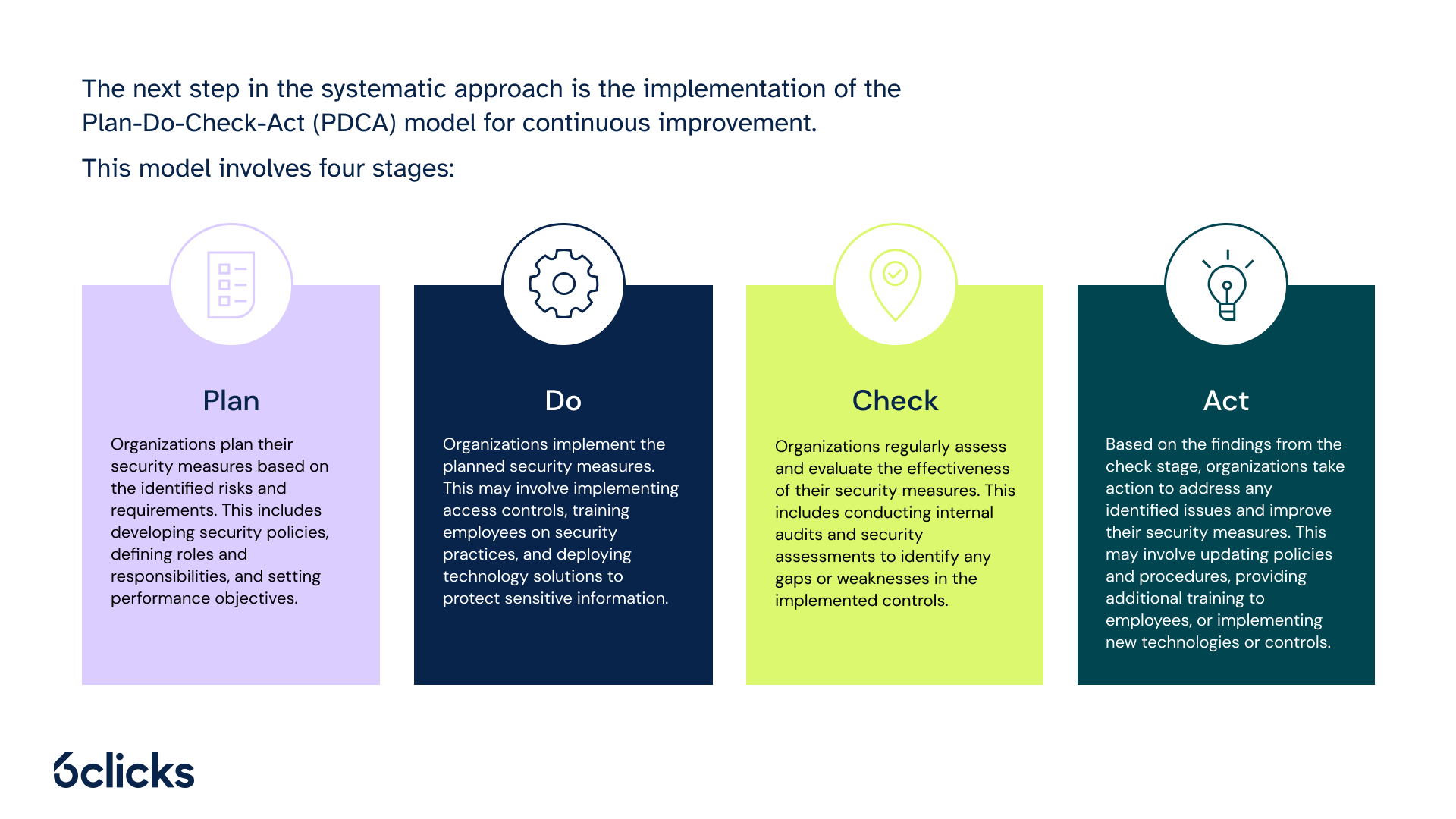
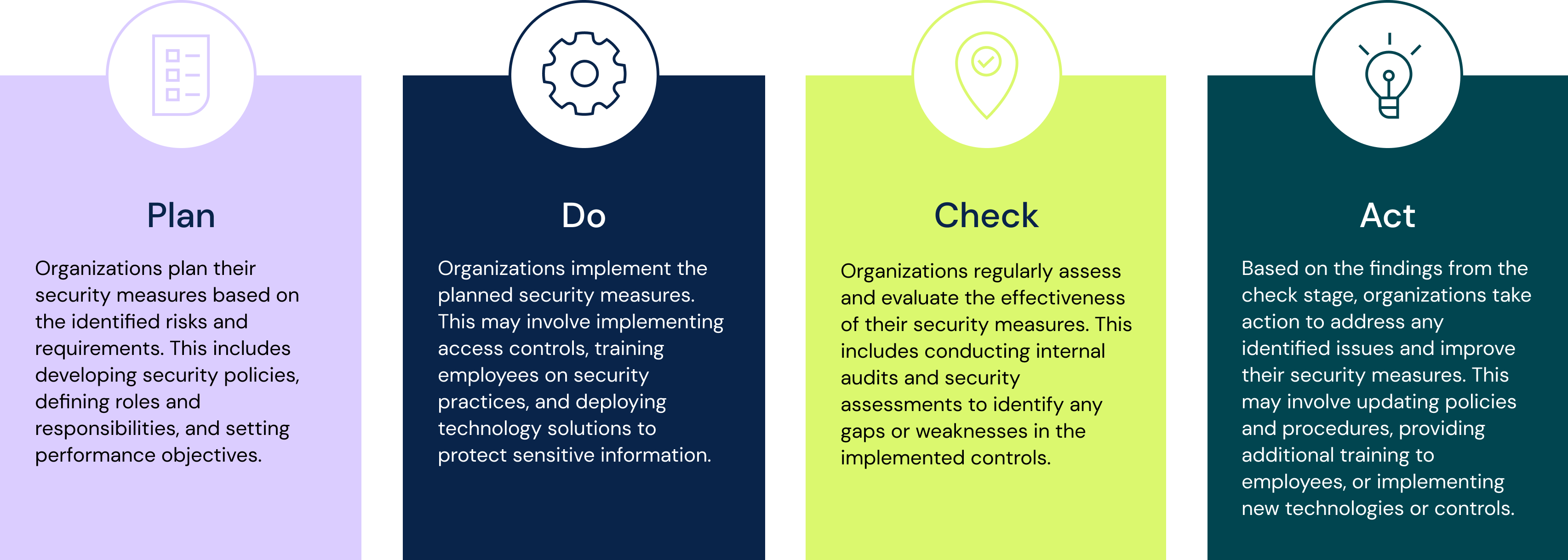
The next step in the systematic approach is the implementation of the Plan-Do-Check-Act (PDCA) model for continuous improvement. This model involves four stages:
- Plan: Organizations plan their security measures based on the identified risks and requirements. This includes developing security policies, defining roles and responsibilities, and setting performance objectives.
- Do: Organizations implement the planned security measures. This may involve implementing access controls, training employees on security practices, and deploying technology solutions to protect sensitive information.
- Check: Organizations regularly assess and evaluate the effectiveness of their security measures. This includes conducting internal audits and security assessments to identify any gaps or weaknesses in the implemented controls.
- Act: Based on the findings from the check stage, organizations take action to address any identified issues and improve their security measures. This may involve updating policies and procedures, providing additional training to employees, or implementing new technologies or controls.
By following this systematic approach, organizations can ensure that their security requirements are effectively addressed and continuously improved. This helps to protect their information and assets from potential security risks and ensures compliance with industry standards and regulatory requirements.
Holistic approach to security management
The holistic approach to security management involves implementing a comprehensive and integrated system to address security risks and controls across the entire organization. Rather than treating security as a standalone function, this approach considers various factors, such as organizational culture, regulatory requirements, and the ever-evolving threat landscape.
By taking a holistic approach, organizations can ensure that security measures are implemented at every level, from physical access controls to data protection protocols. This means that security is not limited to IT departments but is embedded throughout the organization, including human resource security, asset management, and business continuity management.
A key aspect of the holistic approach is the systematic and ongoing nature of security management. It involves regularly assessing and reviewing security risks and controls to identify gaps or weaknesses. This allows organizations to continuously improve and adapt their security measures to address emerging threats and changes in the business environment.
Written by Andrew Robinson
Andrew started his career in the startup world and went on to perform in cyber and information security advisory roles for the Australian Federal Government and several Victorian Government entities. Andrew has a Masters in Policing, Intelligence and Counter-Terrorism (PICT) specialising in Cyber Security and holds IRAP, ISO 27001 LA, CISSP, CISM and SCF certifications.