Unlock the secrets of the NIST Cybersecurity Framework with this comprehensive guide that breaks down its key components and implementation strategies.
Most in-demand frameworks
Other topics

An Overview of the IRAP Assessed GRC Platform for...
What is an IRAP Assessed GRC? An IRAP Assessed GRC platform, or Information Security Registered Assessor Program Assessed Governance, Risk, and Compliance platform, is software..
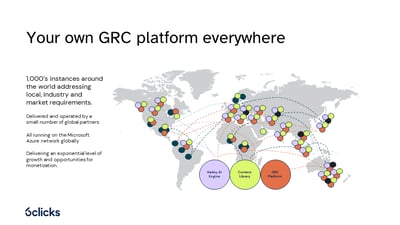
Empowering enterprises: Get in control with your own GRC...
In today's dynamic business landscape, enterprises are constantly seeking innovative solutions to streamline their operations, improve the value they deliver to their customers,..

6clicks Fabric for GSIs: Tailoring cybersecurity GRC...
Robust cybersecurity measures and the effective and safe implementation of IT infrastructure are critical for organizations to successfully do business in the modern digital..

6clicks GRC Platform Now Available on Microsoft Azure for...
New Capability Empowers Global Systems Integrators, Government, and Critical Infrastructure Sectors to Control Configuration, Distribution, Security, and Data Sovereignty

6clicks Fabric: The ultimate control and scale for GRC...
Welcome to the future of GRC management with 6clicks Fabric. In this blog, we'll explore the myriad capabilities and benefits of a 6clicks Fabric instance, from additional control..

Responsible AI: Best practices and real-world examples
In the age of artificial intelligence, not only can algorithms define our digital experiences and influence business decisions, but they are also instrumental in our social..

Responsible AI is here to stay
Artificial Intelligence (AI) and Machine Learning (ML) continue to be a much talked about topic since the release of ChatGPT last year but also well before that to a lesser extent..

Walking the talk: 6clicks Security team's use of 6clicks...
A security-first approach At 6clicks, our unwavering commitment to security and data privacy drives every aspect of our operation. Led by world-class cybersecurity experts,..

ISA/IEC 62443: What is it and how to comply?
What is IEC 62443? IEC 62443 is a series of international standards that focuses on the security of industrial control systems (ICS) and operational technology (OT). With the..






