An information security policy is a requirement in the ISO 27001 standard that aims to demonstrate the commitment of an organization’s executive leadership team to information security. It provides guidance in the development of an Information Security Management System (ISMS) and is a mandatory document for acquiring an ISO 27001 certification. Let’s discuss the components of an ISO 27001 information security policy and how you can create one:
What is an information security policy?
In the context of ISO 27001, an information security policy is created by the top management in an organization to define their objectives for building an Information Security Management System (ISMS).
ISO 27001 is an internationally recognized standard that provides organizations with a framework for establishing, implementing, and maintaining an ISMS. Simply put, an ISMS is comprised of policies, controls, and procedures that dictate how an organization mitigates risks and protects its data and assets from threats. That said, ISO 27001 is centered on enhancing cybersecurity and risk management to uphold data protection and privacy.
The standard provides requirements or “clauses” that organizations must fulfill to ensure their compliance:
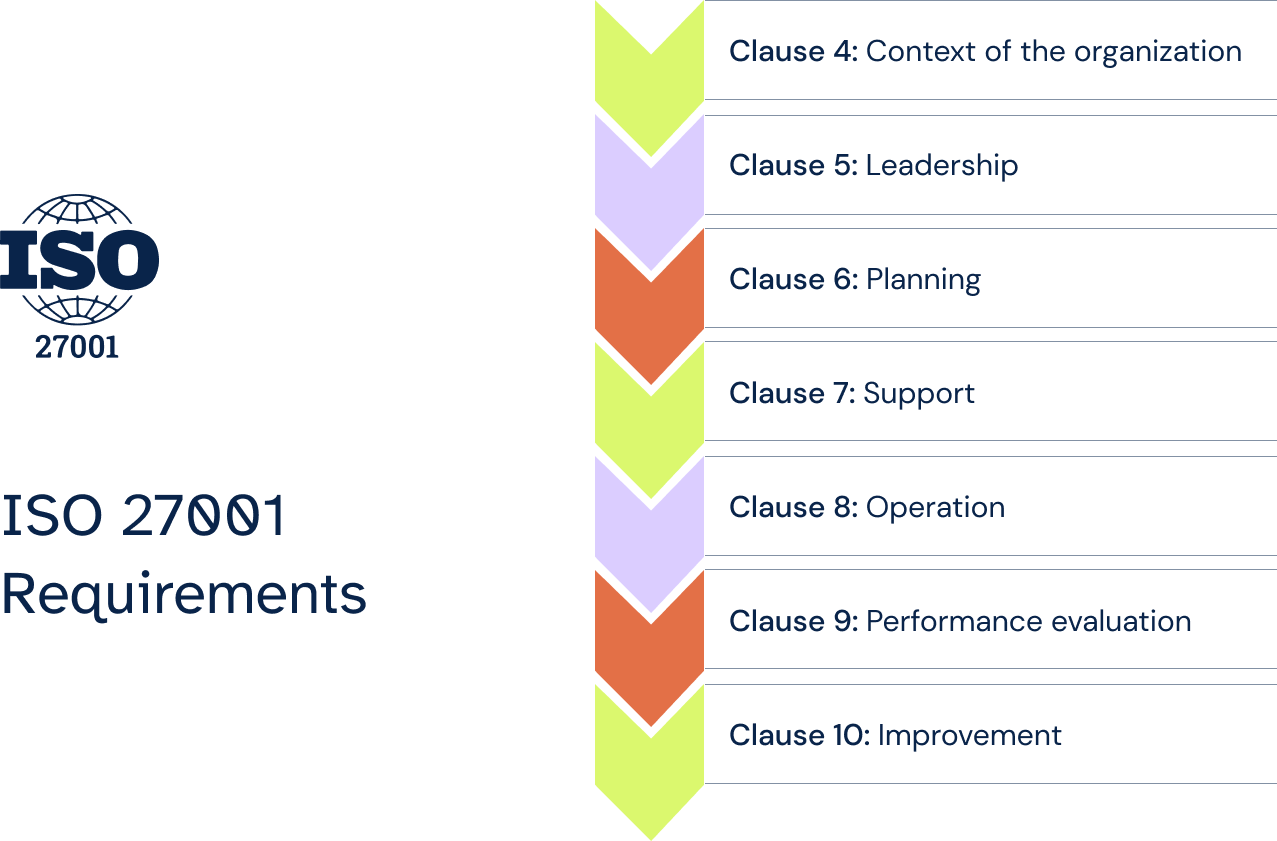
Under Clause 5, organizations must establish leadership guidance and support for the ISMS. This involves the creation of an information security policy, which contains the specifications of the ISMS. The goal of the policy is to assess the level of dedication of the organization’s executive leadership team to maintaining and improving the ISMS.
In the policy, the executive leadership team defines their expected outcomes for the ISMS and the roles and responsibilities that come with its implementation. The policy also serves as a reference for executives to easily obtain high-level details on their organization’s risk management procedures and other core security policies.
What are the contents of an information security policy?
To create an information security policy, executives need to define 5 key components:
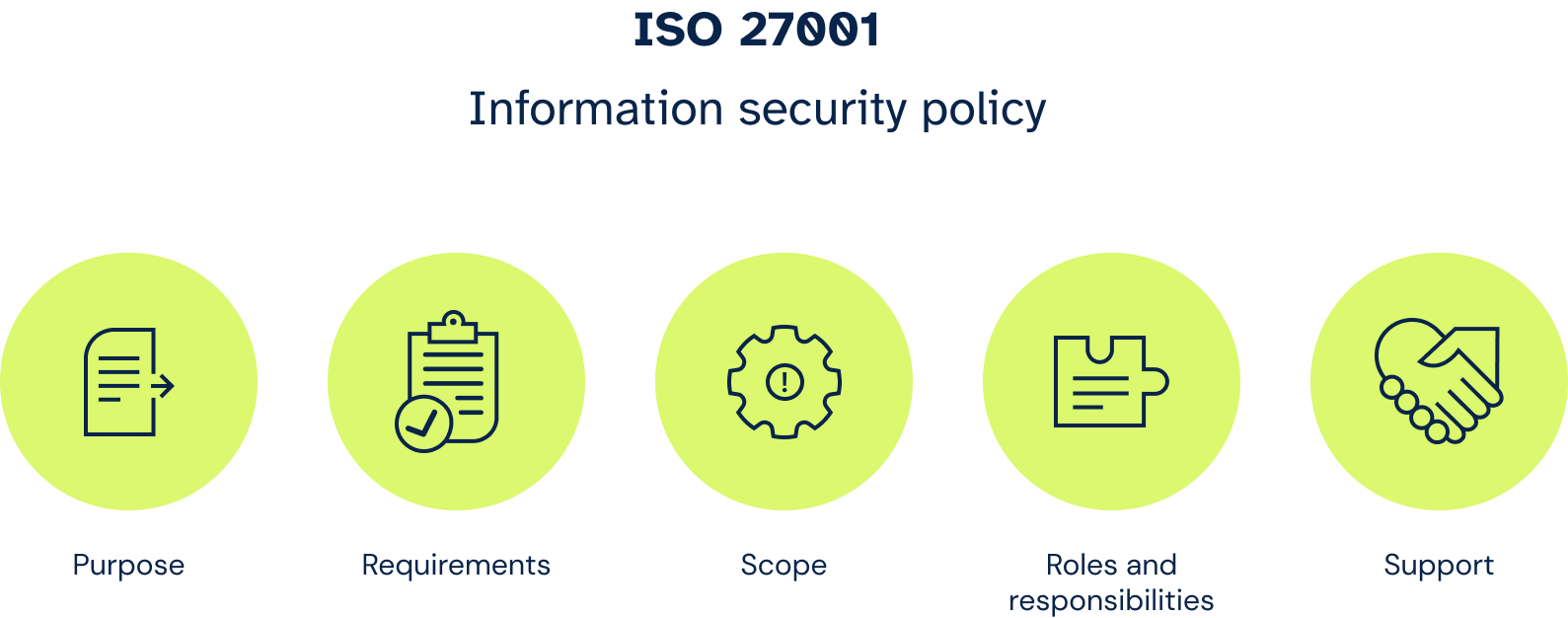
- Purpose – This covers the organization’s general and specific objectives for the ISMS or the conditions that it must meet. General objectives can include the three principles of ISO 27001 that focus on protecting the confidentiality, integrity, and availability of data, whereas specific objectives can address areas like effective third-party risk management and timely incident reporting. Executives also need to specify how the objectives are proposed, reviewed, and approved.
- Requirements – The executive leadership team needs to identify all legal, contractual, and regulatory requirements that the organization must adhere to that have an impact on or are directly related to the development or implementation of the ISMS. These can include agreements with service providers and relevant laws such as the General Data Protection Regulation (GDPR), which shares common requirements and controls for information security with ISO 27001.
- Scope – The main body of an information security policy should tackle the scope of the ISMS. This involves the risk management procedures and security controls that the organization will implement and enforce. Executives must also specify within the scope the "safeguards" or controls delineated in Annex A of ISO 27001 that they will put in place.
- Roles and responsibilities – The executive leadership team must assign designated personnel who will implement and operate the ISMS, who will oversee its maintenance, and who will monitor and report its performance. Additionally, an owner must be assigned to the policy document, and they will be responsible for keeping it up-to-date.
- Support – Lastly, executives need to reference additional resources and supplementary policies that will facilitate the accomplishment of the objectives of the ISMS. This can include other measures and practices that support information security in your organization, such as regular assessments and compliance monitoring.
When formulating their information security policy, the executive leadership team needs to keep in mind that the policy must be tailored to the context of their organization. Looking at aspects like the size of the organization, the industry it operates in, its structure, and operational processes can help you develop an adequate and comprehensive policy.
ISO 27001 requires organizations to write and maintain complete documentation of their information security policy and communicate it to employees, third-party entities, and other relevant stakeholders.
It is also best practice to conduct an annual review of the policy. Corrective changes and updates must be recorded, reviewed, and approved before they make it to the official document.
What is the compliance process for ISO 27001?
The development of an information security policy is just one of the requirements you need to accomplish to become ISO 27001 compliant.
Once you have created your policy, you can then proceed to fulfill the other requirements in the clauses through risk assessment, treatment planning, the implementation of Annex A controls, and the operation of the ISMS. Processes for evaluating and improving the ISMS must also be established and carried out. Afterward, an internal audit must be conducted to determine whether you have met all the requirements of the standard.
ISO 27001 also requires an external audit from a certification body to validate your compliance. Organizations must prepare all necessary documents, such as their information security policy document, documentation of ISMS processes and controls, risk assessment reports, and internal audit reports before going through the certification process.
Achieve ISO 27001 compliance with 6clicks
6clicks’ ISO 27001 solution can empower your organization with robust tools to fast-track the compliance process. Users of the 6clicks platform can download the ISO 27001 framework for free from our Content Library as well as policy and control sets to streamline the development of their information security policy and implementation of ISO 27001 controls.
Meanwhile, 6clicks’ Security Compliance and IT Risk Management solutions offer a variety of tools to augment your risk and compliance processes. Identify and organize your assets using 6clicks’ Asset Management capability and automate risk assessment and treatment planning through our comprehensive risk registers and custom workflows. Then, assign tasks, actions, and responsibilities to key personnel to facilitate ownership and management of the implementation and operation of your ISMS.
Finally, use 6clicks’ Audit and Assessment templates to streamline your internal audit and become well-equipped to secure an ISO 27001 certification.
If you would like to see the 6clicks platform in action and know more about how we can help you achieve compliance with ISO 27001, you can schedule a demo with one of our experts:
Download the ISO 27001 Expert Guide for free
Leverage expert-vetted best practices, tools, and strategies to boost your ISO 27001 compliance. Get your free copy now.
Frequently asked questions
How can I create an information security policy?
To formulate an information security policy, organizations must define the purpose or objectives of their ISMS, their legal, contractual, and regulatory obligations, their risk management policies and procedures and security controls, the roles and responsibilities of key personnel, and additional resources for implementing and operating an ISMS. An information security policy must be based on an organization’s specific context.
Why is ISO 27001 important?
Being ISO 27001 compliant strengthens organizations’ cybersecurity posture, enabling them to effectively manage risks and prevent security incidents such as data breaches, phishing, and malware attacks. It also helps organizations maintain operations and avoid costs and reputational damage amidst disruptions, ensuring business continuity.
What are the benefits of an ISO 27001 certification?
By acquiring an ISO 27001 certification, your organization can showcase its capability to meet rigorous standards and commitment to enhancing its cybersecurity and risk management practices, which can help you enhance customer trust, gain a competitive advantage, and scale your business.
Written by Louis Strauss
Louis is the Co-founder and Chief Product Marketing Officer (CPMO) at 6clicks, where he spearheads collaboration among product, marketing, engineering, and sales teams. With a deep-seated passion for innovation, Louis drives the development of elegant AI-powered solutions tailored to address the intricate challenges CISOs, InfoSec teams, and GRC professionals face. Beyond cyber GRC, Louis enjoys reading and spending time with his friends and family.










