ISO 27001 and NIST CSF both provide organizations with a robust framework for establishing cybersecurity, information security, and data privacy practices and controls to effectively manage and mitigate risks. To determine which framework best suits your needs, it is important to understand both the similarities and differences between the two. Let’s discuss the components of each framework and compare them in terms of their controls, requirements, and intended usage.
What is ISO 27001?
ISO 27001 by the International Organization for Standardization defines requirements for building, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). It was first published in 2005 and recently updated to the 2022 version which introduced a few changes to its controls.
Focusing on three key principles, ISO 27001 aims to safeguard the confidentiality, integrity, and availability of information through the development of an ISMS, which comprises an organization’s policies and procedures for managing sensitive data. The standard is divided into two main parts: the clauses and Annex A. The main requirements for an ISMS are detailed in clauses 4 to 10, which include:
- Understanding the context of the organization
- Establishing objectives for the ISMS and an information security policy through leadership guidance and support
- Planning the ISMS and formulating a risk treatment plan based on risk assessment and security controls
- Preparing support for the ISMS in the form of resources, employee training, and communication with other relevant stakeholders
- Operation of the ISMS by implementing the processes for risk assessment and treatment
- Conducting a performance evaluation to measure, analyze, review, and monitor the effectiveness of the ISMS, and
- Developing a cycle of improvement by continuously correcting nonconformities in the ISMS and eliminating their causes
Annex A, on the other hand, lists a total of 93 controls which are grouped into organizational controls, people controls, physical controls, and technological controls that organizations must implement to comply with the standard.
Essentially, ISO 27001 empowers organizations to become cyber-resilient and achieve operational excellence. It also aligns with other regulations, such as the EU’s General Data Protection Regulation (GDPR), and can facilitate cross-compliance.
Obtaining an ISO 27001 certification enables organizations to gain a competitive advantage as it demonstrates their capacity for enhanced data security.
What is NIST CSF?
While ISO 27001 is a standard for building an information security management system, the National Institute of Standards and Technology’s Cybersecurity Framework (NIST CSF) provides guidelines for developing a cybersecurity risk management and governance program. Released in 2014, the NIST recently published NIST CSF 2.0 in February 2024.
The framework offers organizations actionable steps in achieving desired cybersecurity outcomes, which include managing and minimizing security risks and strengthening their cybersecurity posture. It has three main components: the Core, Profiles, and Tiers.
The CSF Core is composed of 6 functions, which are Govern, Identify, Protect, Detect, Respond, and Recover, that specify the actions that organizations need to take to effectively manage cybersecurity risks. Each function has categories and subcategories that contain the controls of the framework. There are currently a total of 22 categories and 106 controls in NIST CSF 2.0.
The Govern function requires establishing, enforcing, and monitoring the organization’s risk management processes and policies. Meanwhile, the Identify function necessitates an in-depth understanding of the organization’s assets and corresponding cybersecurity risks to enable effective prioritization. Next, the Protect function is where safeguards or controls are utilized to prevent or reduce the likelihood and impact of cyber incidents. Then, in the Detect function, potential cyberattacks are determined and analyzed, which are then addressed in the Respond function. Finally, assets and operations affected by the cyber incident are restored in the Recover function.
Organizations can also assess their current and target cybersecurity posture by creating an Organizational Profile, following the steps outlined in the Profiles section of the framework. Lastly, the CSF Tiers provide organizations with options for implementation, allowing them to define whether their cybersecurity risk management and governance program will have a Partial, Risk-Informed, Repeatable, or Adaptive approach.
What are the similarities between ISO 27001 and NIST CSF?
In addition to being both voluntary frameworks, ISO 27001 and NIST CSF share a primary focus on cybersecurity and risk management.
ISO 27001 and NIST CSF have a significant overlap in terms of practices and controls. Achieving an ISO 27001 certification enables your organization to meet over 80% of the requirements of NIST CSF. Likewise, compliance with NIST CSF can streamline the compliance process for ISO 27001.
Overall, compliance with these two frameworks can provide your organization with comprehensive protection against cyber threats and attacks, help you maintain a robust security posture, and enhance customer trust, ultimately leading to business growth and success.
What are the differences between ISO 27001 and NIST CSF?
Despite their commonalities, there are many differences between ISO 27001 and NIST CSF. Aligning your cybersecurity program with one does not guarantee compliance with the other, and vice versa. Here are some key distinctions between the two frameworks:
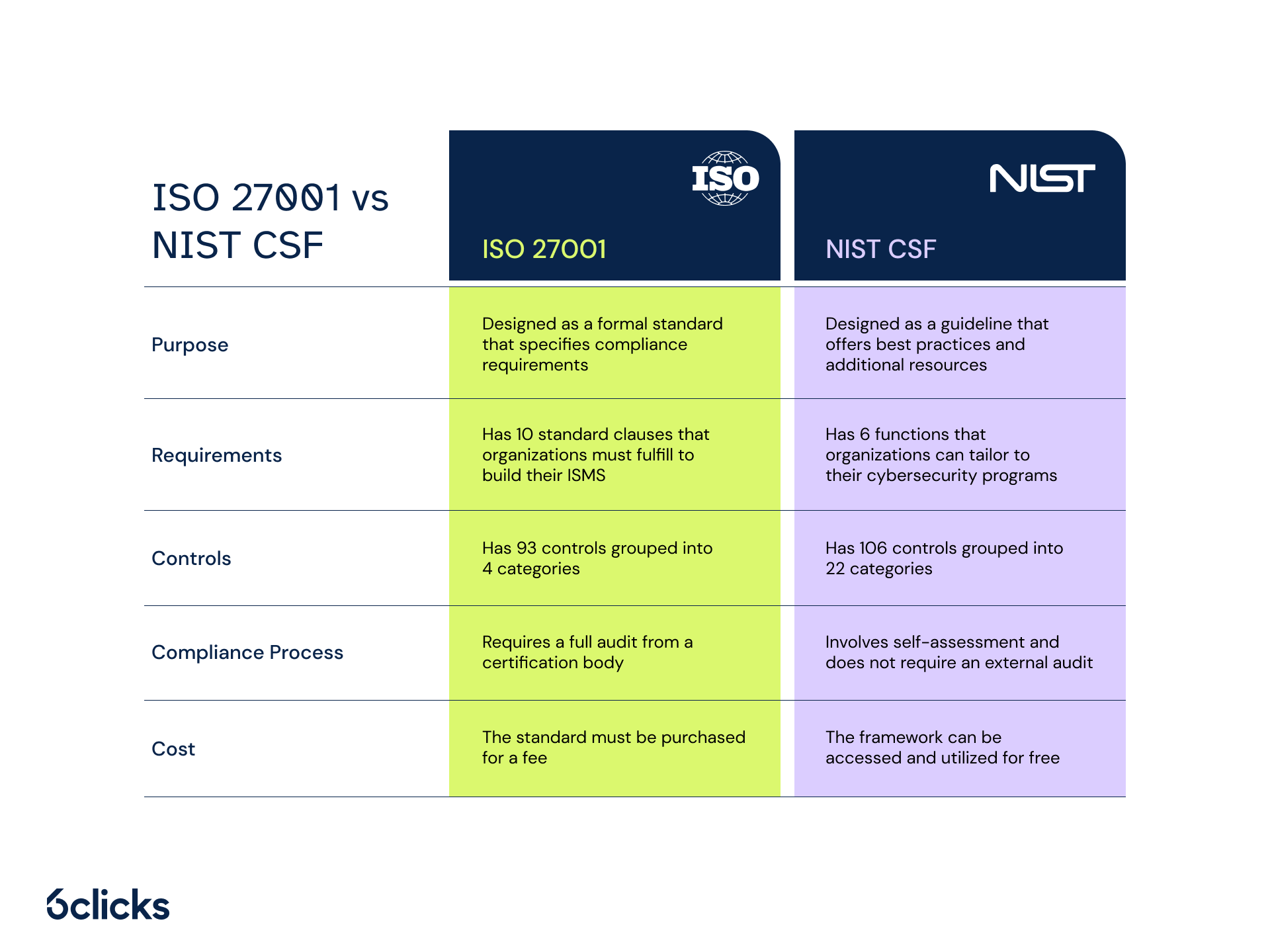
To summarize, NIST CSF offers organizations flexibility and scalability in building their cybersecurity programs, while ISO 27001 is a more rigid framework that provides specific requirements for establishing an effective cybersecurity and risk management strategy.
ISO 27001 or NIST CSF: Which is more suitable for my organization?
Although the two frameworks are generally applicable to organizations of all sizes and from all sectors, enterprises with advanced risk and security maturity tend to opt for ISO 27001 compliance.
NIST CSF is then more ideal for small and midsize businesses looking to start incorporating cybersecurity and risk management into their operations.
If you would like to know how 6clicks can help you secure your organization’s compliance with ISO 27001 or NIST CSF, you can schedule a one-on-one demo with one of our experts by clicking below:
Download the Experts Guide to ISO 27001 compliance
Learn how to establish risk management methodologies that align with your business, how to rapidly complete your ISO 27001 risk assessment, and other tools and strategies to become ISO 27001 compliant.
Frequently asked questions
Why are ISO 27001 and NIST CSF important?
ISO 27001 and NIST CSF serve as a manual for operating cybersecurity processes, tools, and strategies that enable organizations to adeptly address risks, prepare for incidents, and strengthen their resilience to diverse threats while safeguarding valuable data and assets. Both frameworks also facilitate compliance with other standards and regulations such as the GDPR and HIPAA that contain similar controls with ISO 27001 and NIST CSF.
How does the ISO 27001 compliance process work?
First, organizations must develop their ISMS and information security policy through risk assessment, treatment planning, implementation of controls, and the fulfillment of other requirements in ISO 27001. A written document containing all processes, procedures, and controls must also be created, communicated, and maintained. To ensure their compliance with ISO 27001, organizations need to go through an internal audit as well as a full audit conducted by a certification body.
What is 6clicks’ Security Compliance solution?
6clicks’ Security Compliance solution facilitates multi-framework compliance with security frameworks like ISO 27001 and NIST CSF. Using our risk registers, custom workflows, and policy and control management capability, organizations can streamline their risk management processes and implementation of controls based on ISO 27001 requirements. Meanwhile, our audit and assessment templates together with our AI engine Hailey which can automate the generation of audit responses based on previous data, can help you accelerate the compliance process.
Written by Louis Strauss
Louis is the Co-founder and Chief Product Marketing Officer (CPMO) at 6clicks, where he spearheads collaboration among product, marketing, engineering, and sales teams. With a deep-seated passion for innovation, Louis drives the development of elegant AI-powered solutions tailored to address the intricate challenges CISOs, InfoSec teams, and GRC professionals face. Beyond cyber GRC, Louis enjoys reading and spending time with his friends and family.











