An Information Security Management System (ISMS) is designed to safeguard sensitive data and help organizations reduce risks and minimize the impact of cyber incidents. Providing organizations with practices and controls for building an effective ISMS is the primary goal of the ISO 27001 standard. To achieve compliance with ISO 27001, organizations must first understand the significance of developing an ISMS. This article will explore the purpose of an ISMS, the requirements of ISO 27001 for an ISMS, and the benefits of ISO 27001 compliance.
What is an ISMS and why does my organization need one?
Consisting of a set of policies, controls, and procedures for protecting an organization’s data and assets, an ISMS provides a structured approach to managing information security risks. It demonstrates how your organization upholds data privacy and security and responds to cyber threats.
Organizations need an ISMS to proactively identify, prioritize, and treat risks that pose a threat to their assets, stakeholders, and operations. It also helps organizations put security measures and processes in place and define the roles and responsibilities associated with them. In addition, an ISMS:
- Enhances cybersecurity – An ISMS improves the security of Information Technology (IT) systems, networks, and infrastructure, therefore bolstering data protection and privacy
- Offers comprehensive protection – From asset management to risk management to vulnerability and incident management, an ISMS provides a comprehensive approach to cybersecurity
- Prevents security incidents – By staying on top of potential risks, an ISMS can lessen the likelihood and impact of cyberattacks such as data breaches, Denial-of-Service (DoS) attacks, phishing, and malware and ransomware attacks
- Ensures business continuity – An ISMS enhances an organization’s ability to respond to incidents and maintain critical functions during disruptions, preserving your brand reputation and customer trust and fostering operational resilience
- Promotes compliance – Lastly, an ISMS facilitates compliance with regulatory requirements such as those from ISO 27001
All in all, an ISMS supports your organization’s growth and helps you stay ahead of evolving risks and emerging threats.
What is ISO 27001?
The International Organization for Standardization developed ISO 27001, the global standard for building, implementing, maintaining, and continuously improving an ISMS. ISO 27001 offers a holistic approach to information security by addressing all aspects of the organization, including people, processes, and technology. Its latest version is the ISO 27001:2022.
Focusing on cybersecurity, risk management, and privacy protection, ISO 27001 specifies three principles for information security:
- Safeguarding the confidentiality of data
- Preserving the quality or integrity of data
- Ensuring the availability of data
To fulfill these principles, an organization must determine the risks that could impact data and the actions they need to take to mitigate them, hence the need for risk management. By establishing an ISMS and securing compliance with ISO 27001, organizations can effectively manage risks, achieve operational excellence, and become cyber-resilient.
What are the requirements of ISO 27001 for building an ISMS?
ISO 27001 contains the requirements an ISMS must meet, outlined in its Clauses 4 to 10:
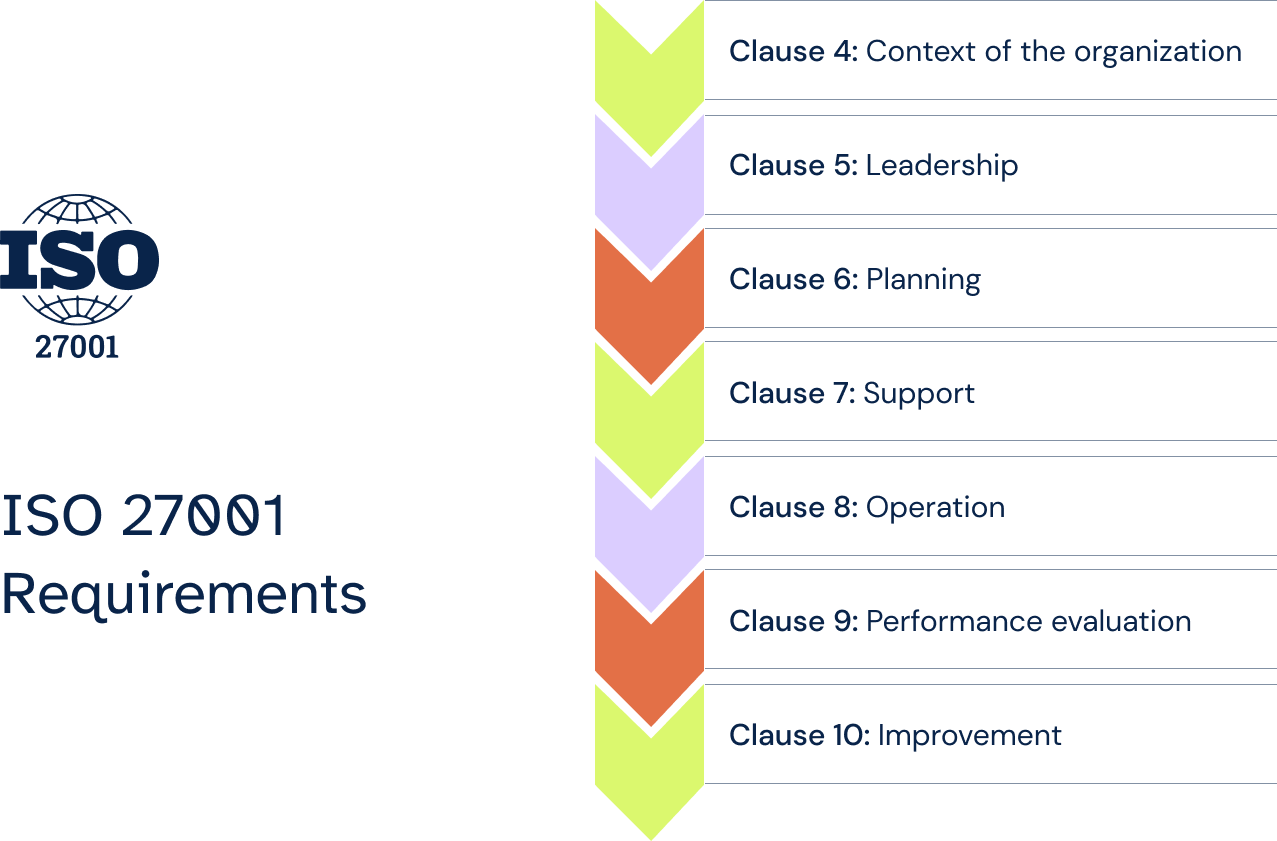
To build an ISMS, ISO 27001 requires an enterprise to first understand the context of its organization – its stakeholders, compliance obligations, and other internal and external factors. Then, objectives for the ISMS as well as an information security policy must be established, documented, and communicated by the executive leadership team. During the planning phase, risks must be assessed in order to create a risk treatment plan. The creation of the ISMS is then supported by the allocation of resources and employee training. Finally, the organization can begin the operation of the ISMS by implementing the processes for risk assessment and treatment. Monitoring and regularly evaluating the ISMS and correcting non-conformities are also imperative to continually improve the organization’s information security and risk management framework.
Meanwhile, Annex A details the safeguards or security controls that organizations must implement, covering critical areas such as asset management, access control, incident management, and third-party risk management. There are 93 controls in ISO 27001, which are categorized under organizational controls, people controls, physical controls, and technological controls. ISO 27001 requires organizations to list all their ISMS controls in a document called the Statement of Applicability.
What are the benefits of being ISO 27001 compliant?
Besides establishing a robust cybersecurity and risk management strategy for your organization, there are many advantages to ensuring your compliance with ISO 27001:
- Compliance with other regulations – ISO 27001 aligns with other industry standards and regulations. For instance, the General Data Protection Regulation (GDPR) also requires organizations to have a security policy, and being compliant with ISO 27001 can help you expedite the compliance process for GDPR.
- Competitive edge – Attaining an ISO 27001 certification showcases your cybersecurity expertise and commitment to safeguarding valuable information, which can help you attract more customers, break into new sectors, and grow your revenue, therefore positioning your organization ahead of competitors.
- Improved credibility – Since ISO 27001 involves external validation of your controls and protocols, being ISO 27001 certified builds trust among stakeholders, customers, and regulators.
- Cost savings – Through your compliance with ISO 27001, you can strengthen your cybersecurity posture and effectively mitigate risks, therefore eliminating potential costs associated with security incidents.
- Strong risk culture – Lastly, being ISO 27001 compliant fosters transparency and accountability and cultivates a culture of risk awareness and management in your organization, empowering you to maintain cyber resilience.
How to become ISO 27001 compliant
Achieving ISO 27001 compliance and certification requires organizations to undergo an internal audit as well as an external audit from a certification body. To prepare for the certification audit, organizations must have complete documentation of their ISMS, information security policy, risk management processes and controls, and internal audit results to ensure they are fully compliant with ISO 27001.
6clicks’ ISO 27001 compliance solution equips organizations with asset and risk management tools to help them perform asset identification, risk assessment, and treatment planning that are necessary for establishing an ISMS. Using 6clicks’ risk and issue libraries, control sets, and audit and assessment templates, organizations can automate their risk management processes and address compliance gaps to fast-track their ISO 27001 certification.
If you need guidance with the certification process or would like to learn more about ISO 27001 and how 6clicks can help you, you can consult with one of our experts by booking a demo below:
Download the ISO 27001 Expert Guide
Get your copy of The Experts Guide for ISO 27001 and your ISMS eBook to gain exclusive access to best practices, tools, and more.
Frequently asked questions
What are the controls in ISO 27001?
Annex A contains the controls of ISO 27001 divided into four themes. Organizational controls include measures implemented at the organizational level, such as your information security policy, the definition of roles and responsibilities, and asset management. People controls cover employee awareness and training, incident reporting procedures, and other processes influenced by human activity in an operational setting. On the other hand, physical controls are those that involve the interaction between people and objects, such as equipment and devices. Finally, technological controls involve network security and segregation, software, and other digital components of information systems.
Is ISO 27001 mandatory?
The ISO 27001 standard is a voluntary framework. However, some countries and industries have made ISO 27001 a legal requirement. Securing compliance with ISO 27001 is necessary for businesses dealing with customer data, such as SaaS providers and data service platforms. Companies in the healthcare, finance, consulting, and information technology sectors that handle personal and sensitive information must also make security their top priority by obtaining an ISO 27001 certification.
What are the documents required for an ISO 27001 certification?
Documents containing the scope of your ISMS and information security policy, risk assessment reports, internal audit reports, and the Statement of Applicability are mandatory documents that organizations need to have for the certification process.
Written by Louis Strauss
Louis is the Co-founder and Chief Product Marketing Officer (CPMO) at 6clicks, where he spearheads collaboration among product, marketing, engineering, and sales teams. With a deep-seated passion for innovation, Louis drives the development of elegant AI-powered solutions tailored to address the intricate challenges CISOs, InfoSec teams, and GRC professionals face. Beyond cyber GRC, Louis enjoys reading and spending time with his friends and family.











