Get certified up to 10x faster at 30% of the cost
Get certified up to 10x faster at 30% of the cost with 6clicks ISMS software. Effectively manage your organization's security processes and compliance requirements with the help of this powerful software solution. Streamline risk assessment, security policy development, and internal audits with a structured and systematic approach. Implement security controls and measures to protect your intellectual property and security assets. The software ensures regulatory compliance and helps you navigate the certification process for ISO/IEC 27001, the international standard for information security management systems. With features such as document management and control, the software allows for easy creation and maintenance of policy documents. It also assists with business continuity management, helping you identify potential risks and develop action plans for corrective actions. The software fosters employee involvement in the security process and facilitates continual improvement. Get certified faster and at a fraction of the cost with ISMS software, gaining a competitive advantage in today's business environment.
Step-by-step guidance to implement your ISMS
Step-by-step guidance is essential when implementing an Information Security Management System (ISMS) to ensure a successful certification process. The preparation phase is the first step in the ISMS implementation journey.
The first task in this phase is to define the certification scope. This involves identifying the boundaries of the ISMS and determining the assets, processes, and departments that will be covered. This step sets the foundation for the rest of the implementation process.
Next, risk assessments are conducted to identify potential threats and vulnerabilities. This helps in understanding the potential impact on the organization's information security and prioritizing controls accordingly. A comprehensive risk assessment helps to create an effective risk management framework.
The final step in the preparation phase is designing controls. Based on the results of the risk assessment, appropriate security controls are selected and implemented. These controls are designed to mitigate the identified risks and protect the organization's information assets.
Each step in the preparation phase contributes to the overall goal of achieving certification success. Defining the certification scope ensures that the ISMS covers all necessary areas of the organization. Conducting risk assessments helps prioritize the implementation of controls based on the identified risks, ensuring that resources are allocated correctly. Designing controls aims to provide a structured and systematic approach to managing security risks.
By following this step-by-step guidance, organizations can effectively implement their ISMS, reducing security risks and ensuring regulatory compliance. This, in turn, enhances their competitive advantage and protects their intellectual property and other critical assets.
Powered by artificial intelligence to get more done
In today's fast-paced world, getting more done in less time is a constant challenge for individuals and businesses alike. Fortunately, the advancements in technology, particularly the integration of artificial intelligence (AI), have revolutionized the way we work and boosted productivity to unprecedented levels.
One of the standout applications of AI in productivity enhancement is the development of software powered by artificial intelligence. This cutting-edge technology combines the capabilities of machine learning, natural language processing, and data analysis to automate and streamline various tasks, enabling individuals and organizations to achieve more in a shorter amount of time.
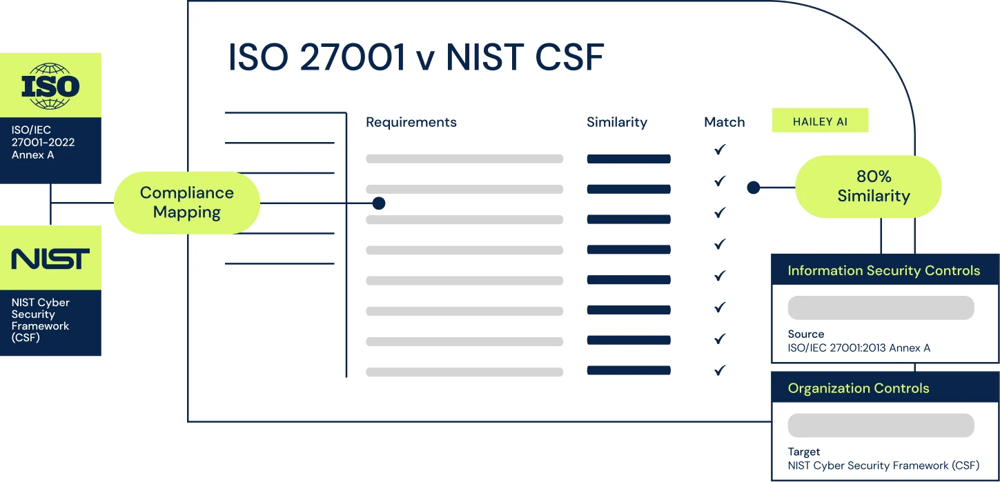
6clicks is powered by Hailey, our AI engine, designed to automate and streamline risk and compliance. Learn more about Hailey, the 6clicks AI engine here.
.
Hailey supports risk and compliance professionals with compliance mapping between standards, laws and regulations, control set mapping back to compliance obligations to help identify areas of compliance and non-compliance, and control definitions by leveraging the Open AI's GPT technology, saving your team hours of manual work.
Supporting 100's of frameworks, standards & regulations
Supporting 100's of frameworks, standards & regulations, implementing an Information Security Management System (ISMS) can be a complex task. However, by following a systematic approach and utilizing the right tools and software, organizations can successfully implement an ISMS and achieve certification.
To begin the implementation process, it is essential to define the scope of certification. This involves identifying the systems, processes, and assets that need to be protected and determining the boundaries within which the ISMS will be implemented. Defining the scope helps in setting clear objectives and ensures that the efforts are focused on the most critical areas.
The next step is to perform a thorough risk assessment. This involves identifying potential threats and vulnerabilities, assessing their impact on the organization, and prioritizing them based on their likelihood and potential consequences. A comprehensive risk assessment enables organizations to understand their current security posture and identify areas that require immediate attention.
Once the risks have been identified, the next step is to design controls to mitigate those risks. This involves selecting appropriate security measures and implementing them in a structured and systematic manner. It is essential to ensure that the controls are aligned with industry best practices and meet the requirements of relevant standards and regulations.
To ensure a successful certification outcome, it is crucial to follow a systematic approach throughout the implementation process. The Assured Results Method provides step-by-step guidance and frameworks that enable organizations to efficiently implement an ISMS. This includes preparing for the implementation, conducting risk assessments, designing controls, and continually improving the information security management system.
By following a systematic approach and utilizing ISMS software, organizations can streamline the implementation process, reduce manual effort, and ensure compliance with various frameworks, standards, and regulations. Additionally, the software provides features such as document management, action plans, and asset registers, which further enhance the effectiveness of the ISMS implementation process.
Where to start with 6clicks
When starting the implementation of an effective information security management system (ISMS), a robust software solution like 6clicks can provide valuable support by offering a comprehensive list of supported frameworks, standards, and regulations. With 6clicks, users can confidently navigate through the complexities of information security compliance and risk management.
6clicks supports hundreds of frameworks, standards, and regulations, including ISO/IEC 27001, NIST Cyber Security Framework, BSI Standards, IT-Security Baseline, CIS Controls, and PCI-DSS. This ensures that organizations can effectively comply with various industry requirements and best practices without the need for multiple tools or manual processes.
Furthermore, through 6clicks, users can develop their ISO 27001 ISMS policy and SMART (Specific, Measurable, Achievable, Relevant, Time-bound) objectives. The software assists in defining clear policies and objectives that align with the organization's strategic goals. It also helps track and monitor the progress of these objectives, ensuring that they are achieved within the planned timeframe.
With 6clicks, organizations can streamline their information security management processes, simplify compliance efforts, and proactively mitigate risks. By leveraging its supporting frameworks, standards, and regulations, such as ISO/IEC 27001, NIST Cyber Security Framework, BSI Standards, IT-Security Baseline, CIS Controls, and PCI-DSS, organizations can effectively protect their valuable assets and maintain a strong security posture.
Written by Andrew Robinson
Andrew started his career in the startup world and went on to perform in cyber and information security advisory roles for the Australian Federal Government and several Victorian Government entities. Andrew has a Masters in Policing, Intelligence and Counter-Terrorism (PICT) specialising in Cyber Security and holds IRAP, ISO 27001 LA, CISSP, CISM and SCF certifications.